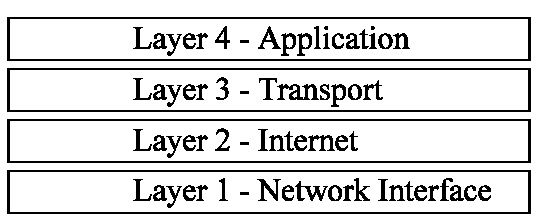
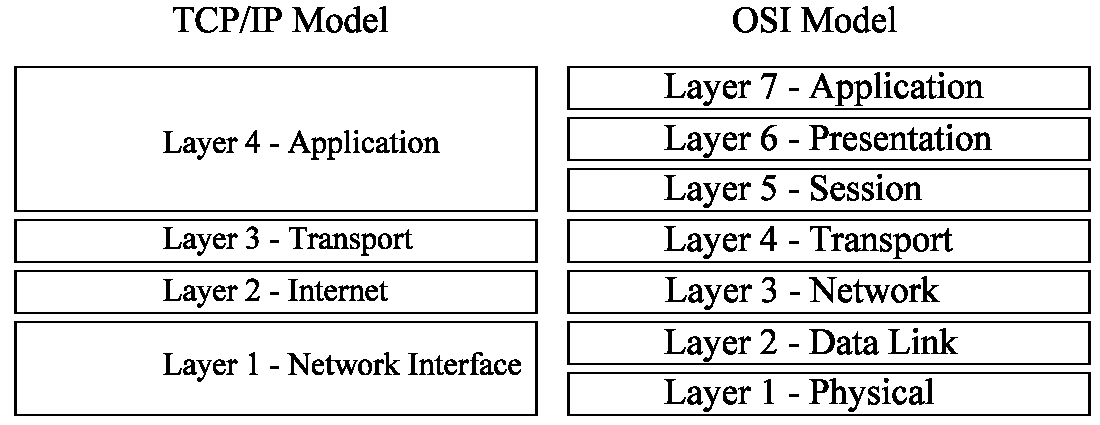
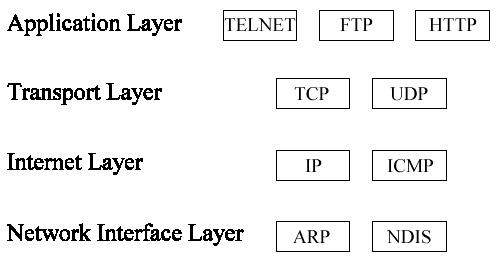
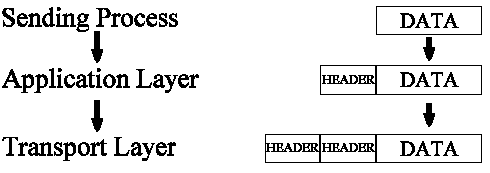
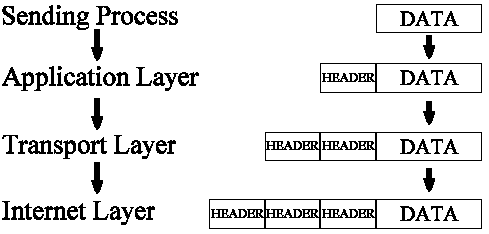
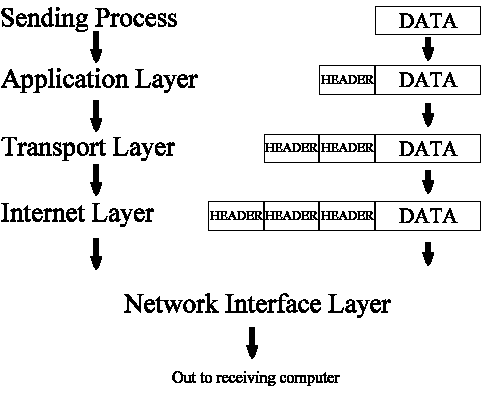
Layer 2 protocols (Data Link Layer)
ARCnet Attached Resource Computer NETwork
CDP Cisco Discovery Protocol
DCAP Data Link Switching Client Access Protocol
Distributed Multi-Link Trunking
Distributed Split Multi-Link Trunking
Dynamic Trunking Protocol
Econet
Ethernet
FDDI Fiber Distributed Data Interface
Frame Relay
ITU-T G.hn Data Link Layer
HDLC High-Level Data Link Control
IEEE 802.11 WiFi
IEEE 802.16 WiMAX
LACP Link Aggregation Control Protocol
LattisNet
LocalTalk
L2F Layer 2 Forwarding Protocol
L2TP Layer 2 Tunneling Protocol
LAPD Link Access Procedures on the D channel
LLDP Link Layer Discovery Protocol
LLDP-MED Link Layer Discovery Protocol - Media Endpoint Discovery
PAgP - Cisco Systems proprietary link aggregation protocol
PPP Point-to-Point Protocol
PPTP Point-to-Point Tunneling Protocol
Q.710 Simplified Message Transfer Part
Multi-link trunking Protocol
RPR IEEE 802.17 Resilient Packet Ring
SLIP Serial Line Internet Protocol (obsolete)
StarLAN
STP Spanning Tree Protocol
Split multi-link trunking Protocol
Token ring a protocol developed by IBM; the name can also be used to describe the token passing ring logical topology that it popularized.
VTP VLAN Trunking Protocol
Layer 2+3 protocols
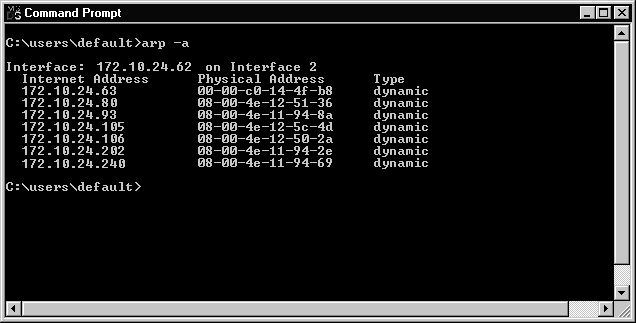
ARP Address Resolution Protocol
RARP Reverse Address Resolution Protocol
ATM Asynchronous Transfer Mode
Frame relay, a simplified version of X.25 welcome
MPLS Multi-protocol label switching
SPB Shortest Path Bridging
X.25
MTP Message Transfer Part
NSP Network Service Part
Layer 3 protocols (Network Layer)
CLNP Connectionless Networking Protocol
EGP Exterior Gateway Protocol
EIGRP Enhanced Interior Gateway Routing Protocol
IGMP Internet Group Management Protocol
IGRP Interior Gateway Routing Protocol
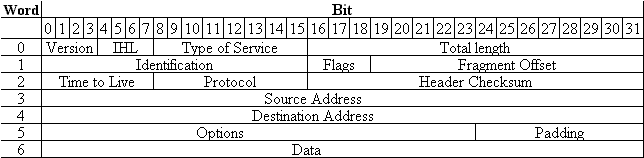
IPv4 Internet Protocol version 4
IPv6 Internet Protocol version 6
IPSec Internet Protocol Security
IPX Internetwork Packet Exchange
Routed-SMLT
SCCP Signalling Connection Control Part
AppleTalk DbP
Layer 3 protocols (Network Layer management)
IS-IS Intermediate System-to-Intermediate System
OSPF Open Shortest Path First
NDP Neighbor Discovery Protocol
Gateway Discovery Protocol (GDP) is a Cisco protocol similar to IRDP
IGRP
EIGRP
ICMP
L2 or L3 protocol like OSPF, BGP,ISIS, RIP,MPLS, DSL,ADSL, SDH,Sonet, DSLAM,VLAN,ATM,QoS,framerelay,
Layer 3.5 protocols
HIP Host Identity Protocol
Layer 3+4 protocol suites
AppleTalk
DECnet
IPX/SPX
Internet Protocol Suite
Xerox Network Systems
Layer 4 protocols (Transport Layer)
AH Authentication Header over IP or IPSec
ESP Encapsulating Security Payload over IP or IPSec
GRE Generic Routing Encapsulation for tunneling
IL Originally developed as transport layer for 9P
SCTP Stream Control Transmission Protocol
Sinec H1 for telecontrol
SPX Sequenced Packet Exchange
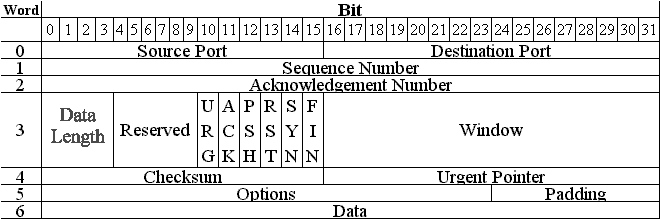
TCP Transmission Control Protocol
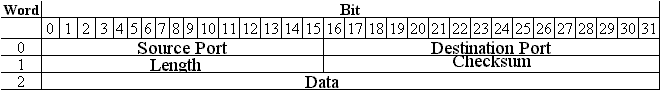
UDP User Datagram Protocol
DCCP Datagram Congestion Control Protocol
Layer 5 protocols (Session Layer)
9P Distributed file system protocol developed originally as part of Plan 9
NCP NetWare Core Protocol
NFS Network File System
SMB Server Message Block
SOCKS "SOCKetS"
Other protocols
Controller Area Network (CAN)
Layer 7 protocols (Application Layer)
ADC, A peer-to-peer file sharing protocol
AFP, Apple Filing Protocol
BACnet, Building Automation and Control Network protocol
BitTorrent, A peer-to-peer file sharing protocol
BGP Border Gateway Protocol
BOOTP, Bootstrap Protoc;
CAMEL, an SS7 protocol tool for the home operator
Diameter, an authentication, authorization and accounting protocol
DICOM includes a network protocol definition
DICT, Dictionary protocol
DNS, Domain Name System
DSM-CC Digital Storage Media Command and Control
DSNP, Distributed Social Networking Protocol
DHCP, Dynamic Host Configuration Protocol
ED2K, A peer-to-peer file sharing protocol
FTP, File Transfer Protocol
Finger, which gives user profile information
Gnutella, a peer-to-peer file-swapping protocol
Gopher, a hierarchical hyperlinkable protocol
HTTP, Hypertext Transfer Protocol
HTTPS, Hypertext Transfer Protocol Secure
IMAP, Internet Message Access Protocol
IRC, Internet Relay Chat
ISUP, ISDN User Part
LDAP Lightweight Directory Access Protocol
MIME, Multipurpose Internet Mail Extensions
MSNP, Microsoft Notification Protocol (used by Windows Live Messenger)
MAP, Mobile Application Part
NetBIOS, File Sharing and Name Resolution protocol - the basis of file sharing with Windows.
NNTP, Network News Transfer Protocol
NTP, Network Time Protocol
NTCIP, National Transportation Communications for Intelligent Transportation System Protocol
POP3 Post Office Protocol Version 3
RADIUS, an authentication, authorization and accounting protocol
RDP, Remote Desktop Protocol
Rlogin, a UNIX remote login protocol
rsync, a file transfer protocol for backups, copying and mirroring
RTP, Real-time Transport Protocol
RTSP, Real-time Transport Streaming Protocol
SSH, Secure Shell
SISNAPI, Siebel Internet Session Network API
SIP, Session Initiation Protocol, a signaling protocol
SMTP, Simple Mail Transfer Protocol
SNMP, Simple Network Management Protocol
SOAP, Simple Object Access Protocol
SMB, Microsoft Server Message Block Protocol
STUN, Session Traversal Utilities for NAT
TUP, Telephone User Part
Telnet, a remote terminal access protocol
TCAP, Transaction Capabilities Application Part
TFTP, Trivial File Transfer Protocol, a simple file transfer protocol
WebDAV, Web Distributed Authoring and Versioning
XMPP, an instant-messaging protocol