Hack Websites Using SQL Poizon and Havij
Requirements:
- A Brain ( Most Important )
- SQL Poizon ( Download )
- Havij 1.6 Pro ( Cracked Version Download )
- Basic Knowledge about Websites and SQL Injection
I
did not make these programs, nor did I most likely download them from
the original source. If you do not trust these, then just sandbox them.
You can download Sandboxie . Also the download to Havij is the pro/full version cracked. Want the regular one from the developers? Download Here
All Right, now that we have whatever we need, let the Tutorial BEGIN !! :)
Step 1 : Open up SQL Poizon
Step 2 : Click the "+" next to “All Dork" or just double click on “All Dorks". Next, select php. In the php section select “page.php?id="
Then, select “Engine:" then in “Engine:" select “Searchqu" you can put “max" whatever you’d like, but I put mine at 300. Note: “max" is the max amount of results your dork search will pull in. Sql poizon searches for websites with that dork that have sql vulnerabilities.
Then, select “Engine:" then in “Engine:" select “Searchqu" you can put “max" whatever you’d like, but I put mine at 300. Note: “max" is the max amount of results your dork search will pull in. Sql poizon searches for websites with that dork that have sql vulnerabilities.
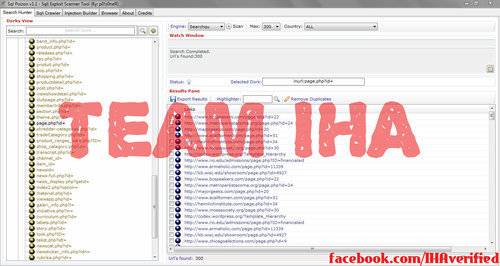
Step 3 : Right
click on one of the links, then hover over “Send to Sqli Crawler".
Next, select “All". After this you will be brought to a screen that
looks like the one below. You will then want to click on crawl. Sql
poizon will crawl through the Searchqu search engine, search your dork,
and find any websites that are vulnerable or could be vulnerable to an
attack.
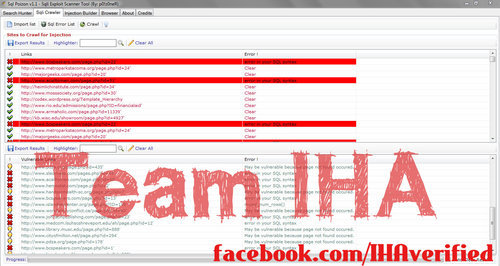
Step 4 : View a couple of the vulnerable websites in the “Vulnerable Links" box on the bottom half of Sql poizon.

Then, select the website you’d like to hack. Copy the url without the ’
(the apostrophe). Open up Havij and click register. For name enter:
“Cracked@By.Exidous" and for file find you folder location where havij
is and choose “HavijKey.lic". You will now have Havij Pro.
Step 5:
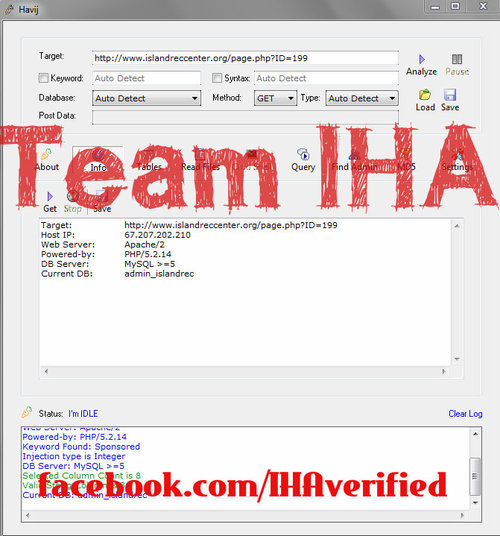
Find “Target:" and paste your vulnerable website in there.
Leave the rest by default and click “Analyze".
In the box at the bottom you will find information on your target such as:
- Host IP (Target website’s ip address)
- Web Server (What web server your target runs on)
- Powered-By (What your target is powered by generally php or asp)
- Keyword Found (A keyword about your target)
- Injection Type (The type of injection that Havij will use)
- DB Server (The type of database your target uses)
- Current DB (The database that havij detected)
Note: You may have more or less things displayed depending on your
target website. You can also find your target info by going to the
“Info" tab.
Step 6 : Click on the “Tables" tab, and hit “Get DBs". Once your target’s databases have loaded go ahead and find a table that looks like it could have interesting information, logins, admin info, or anything you’d like to snoop in.

I’ll be taking some customer info so I am going to my “customer" table.
Once, you select your desired table go ahead and click “Get Columns".
Havij will then proceed to get all of the columns in that table. Once
Havij loads the columns check each column you’d like to collect the data
from. Click “Get Data" and Havij will get information stored in each
column from the table you selected. Since I selected the “customer"
table from my “targets" database, Havij got data that included: ID,
parentName, street, city, state, zip, homephone, workphone, emergphone,
emergname, email, password, newsletter, savelogin, and ageNotice.
Step 7 :
Next I will be finding the admin’s data in an attempt to login in to
his cpanel or admin login. So, find a table that looks like it could
possibly admin or login. Anything of that sort will do. My table’s name
that the login is stored in is called “logins". I then checked “logins"
and pressed “Get Columns". Then, I proceeded to check each column and
hit “Get Data".
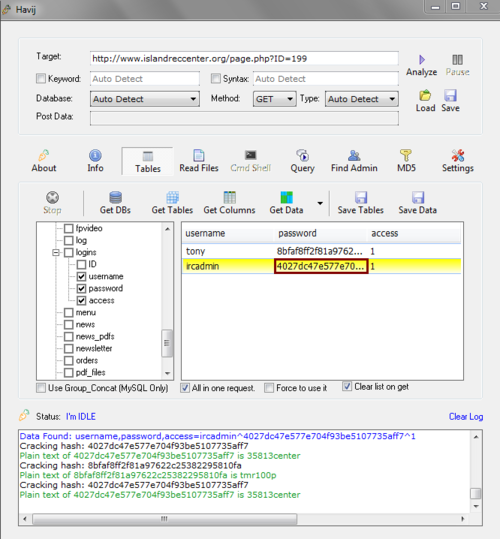
Step 8 : Once
I found the username and the password I had to decrypt the md5
encryption. To do this Havij has a built in MD5 Decrypter. Copy the
password, and click “MD5".
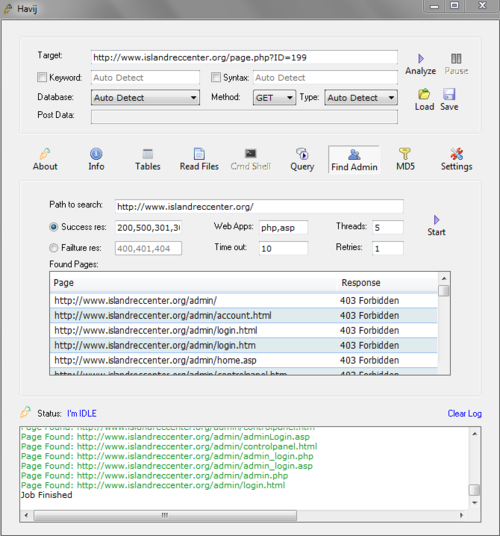
Step 9 : Now we need to find the admin login. To do this we need to click on the “Find Admin" tab. After that just click “start". If you need a different program you can use this one with a bigger admin text file, but I still prefer to use Havij’s built in one. But if you want, you can download Admin Finder from HERE
Step 10 : Finally, once you have found the admin login username and password, and the admin login page just go ahead and login! From there do whatever you’d like! Note: If you did not ever find the admin login information you may be able to find it by causing an error in the webpage. You might get an error like the following:
"Warning: mysql_fetch_array(): supplied argument is not a valid MySQL result resource in /home/admin/domains/yourtarget.org/public_html/page.php on line 14But if you are Lucky Enough You might HIT the Jackpot LIKE me ! :)
No comments:
Post a Comment