| Capstone
| A now-defunct U.S. National Institute
of Standards and Technology (NIST) and National Security Agency (NSA)
project under the Bush Sr. and Clinton administrations for publicly
available strong cryptography with keys escrowed by the government (NIST
and the Treasury Dept.). Capstone included in one or more tamper-proof
computer chips for implementation (Clipper), a secret key encryption
algorithm (Skipjack), digital signature algorithm (DSA), key exchange
algorithm (KEA), and hash algorithm (SHA).
|
| Clipper
| The computer chip that would implement the Skipjack encryption scheme. See also EPIC's The Clipper Chip Web page.
|
| Escrowed Encryption Standard (EES)
| Largely unused, a controversial crypto
scheme employing the SKIPJACK secret key crypto algorithm and a Law
Enforcement Access Field (LEAF) creation method. LEAF was one part of
the key escrow system and allowed for decryption of ciphertext messages
that had been legally intercepted by law enforcement agencies. Described
more in FIPS 185.
|
| Federal Information Processing Standards (FIPS)
| These computer security- and
crypto-related FIPS are produced by the U.S. National Institute of
Standards and Technology (NIST) as standards for the U.S. Government.
|
| Fortezza (formerly called Tessera)
| A PCMCIA card developed by NSA that
implements the Capstone algorithms, intended for use with the Defense
Messaging Service (DMS).
|
| GOST
| GOST is a family of algorithms that is
defined in the Russian cryptographic standards. Although most of the
specifications are written in Russian, a series of RFCs describe some of
the aspects so that the algorithms can be used effectively in Internet
applications:
- RFC 4357:
Additional Cryptographic Algorithms for Use with GOST 28147-89, GOST R
34.10-94, GOST R 34.10-2001, and GOST R 34.11-94 Algorithms
- RFC 5830: GOST 28147-89: Encryption, Decryption, and Message Authentication Code (MAC) Algorithms
- RFC 6986: GOST R 34.11-2012: Hash Function Algorithm
- RFC 7091: GOST R 34.10-2012: Digital Signature Algorithm (Updates RFC 5832: GOST R 34.10-2001)
|
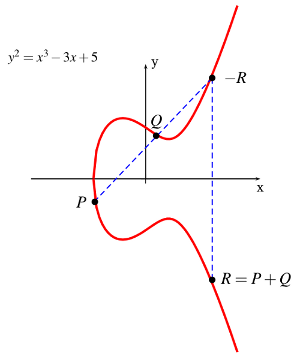
| Identity-Based Encryption (IBE)
|
Identity-Based Encryption was first proposed by Adi Shamir in 1984, and
is a key authentication system where the public key can be derived from
some unique information based upon the user's identity. In 2001, Dan
Boneh (Stanford) and Matt Franklin (U.C., Davis) developed a practical
implementation of IBE based on elliptic curves and a mathematical
construct called the Weil Pairing. In that year, Clifford Cocks (GCHQ)
also described another IBE solution based on quadratic residues in
composite groups.
|
| IP Security Protocol (IPsec)
| The IPsec protocol suite is used to
provide privacy and authentication services at the IP layer. An overview
of the protocol suite and of the documents comprising IPsec can be
found in RFC 2411. Other documents include:
- RFC 4301: IP security architecture.
- RFC 4302:
IP Authentication Header (AH), one of the two primary IPsec functions;
AH provides connectionless integrity and data origin authentication for
IP datagrams and protects against replay attacks.
- RFC 4303:
IP Encapsulating Security Payload (ESP), the other primary IPsec
function; ESP provides a variety of security services within IPsec.
- RFC 4304:
Extended Sequence Number (ESN) Addendum, allows for negotiation of a
32- or 64- bit sequence number, used to detect replay attacks.
- RFC 4305: Cryptographic algorithm implementation requirements for ESP and AH.
- RFC 5996:
The Internet Key Exchange (IKE) protocol, version 2, providing for
mutual authentication and establishing and maintaining security
associations.
- IKE v1 was described in three separate documents, RFC 2407 (application of ISAKMP to IPsec), RFC 2408 (ISAKMP, a framework for key management and security associations), and RFC 2409
(IKE, using part of Oakley and part of SKEME in conjunction with ISAKMP
to obtain authenticated keying material for use with ISAKMP, and for
other security associations such as AH and ESP). IKE v1 is obsoleted
with the introdcution of IKEv2.
- RFC 4307: Cryptographic algoritms used with IKEv2.
- RFC 4308: Crypto suites for IPsec, IKE, and IKEv2.
- RFC 4309: The use of AES in CBC-MAC mode with IPsec ESP.
- RFC 4312: The use of the Camellia cipher algorithm in IPsec.
- RFC 4359: The Use of RSA/SHA-1 Signatures within Encapsulating Security Payload (ESP) and Authentication Header (AH).
- RFC 4434: Describes AES-XCBC-PRF-128, a pseudo-random function derived from the AES for use with IKE.
- RFC 2403: Describes use of the HMAC with MD5 algorithm for data origin authentication and integrity protection in both AH and ESP.
- RFC 2405: Describes use of DES-CBC (DES in Cipher Block Chaining Mode) for confidentiality in ESP.
- RFC 2410: Defines use of the NULL encryption algorithm (i.e., provides authentication and integrity without confidentiality) in ESP.
- RFC 2412: Describes OAKLEY, a key determination and distribution protocol.
- RFC 2451: Describes use of Cipher Block Chaining (CBC) mode cipher algorithms with ESP.
- RFCs 2522 and 2523: Description of Photuris, a session-key management protocol for IPsec.
In addition, RFC 6379 describes Suite B Cryptographic Suites for IPsec and RFC 6380 describes the Suite B profile for IPsec.
IPsec was first proposed for use with IP version 6 (IPv6), but can also be employed with the current IP version, IPv4.
(See more detail about IPsec below in Section 5.6.) |
| Internet Security Association and Key Management Protocol (ISAKMP/OAKLEY)
| ISAKMP/OAKLEY provide an infrastructure for Internet secure communications. ISAKMP, designed by the National Security Agency (NSA) and described in RFC 2408,
is a framework for key management and security associations,
independent of the key generation and cryptographic algorithms actually
employed. The OAKLEY Key Determination Protocol, described in RFC 2412, is a key determination and distribution protocol using a variation of Diffie-Hellman.
|
| Kerberos
| A secret-key encryption and
authentication system, designed to authenticate requests for network
resources within a user domain rather than to authenticate messages.
Kerberos also uses a trusted third-party approach; a client
communications with the Kerberos server to obtain "credentials" so that
it may access services at the application server. Kerberos V4 uses DES
to generate keys and encrypt messages; DES is also commonly used in
Kerberos V5, although other schemes could be employed.
Microsoft added support for Kerberos V5 — with some proprietary
extensions — in Windows 2000. There are many Kerberos articles posted at
Microsoft's Knowledge Base, notably "Basic Overview of Kerberos User Authentication Protocol in Windows 2000," "Windows 2000 Kerberos 5 Ticket Flags and KDC Options for AS_REQ and TGS_REQ Messages," and "Kerberos Administration in Windows 2000."
|
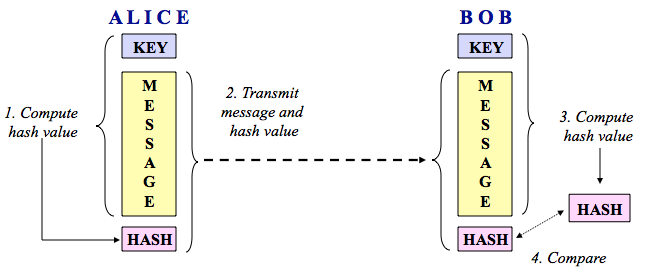
| Keyed-Hash Message Authentication Code (HMAC)
| A message authentication scheme based
upon secret key cryptography and the secret key shared between two
parties rather than public key methods. Described in FIPS 198 and RFC 2104.
|
| Message Digest Cipher (MDC)
| Invented by Peter Gutman, MDC turns a one-way hash function into a block cipher.
|
| MIME Object Security Standard (MOSS)
| Designed as a successor to PEM to provide PEM-based security services to MIME messages.
|
| NSA Suite B Cryptography
| An NSA standard for securing information at the SECRET level. Defines use of:
- Advanced Encryption Standard (AES) with key sizes of 128 and 256 bits, per FIPS PUB 197 for encryption
- The Ephemeral Unified Model and the One-Pass Diffie Hellman
(referred to as ECDH) using the curves with 256 and 384-bit prime
moduli, per NIST Special Publication 800-56A for key exchange
- Elliptic Curve Digital Signature Algorithm (ECDSA) using the curves with 256 and 384-bit prime moduli, per FIPS PUB 186-3 for digital signatures
- Secure Hash Algorithm (SHA) using 256 and 384 bits, per FIPS PUB 180-3 for hashing
RFC 6239 describes Suite B Cryptographic Suites for Secure Shell (SSH) and RFC 6379 describes Suite B Cryptographic Suites for Secure IP (IPsec).
|
| Pretty Good Privacy (PGP)
| A family of cryptographic routines for
e-mail and file storage applications developed by Philip Zimmermann.
PGP 2.6.x uses RSA for key management and digital signatures, IDEA for
message encryption, and MD5 for computing the message's hash value; more
information can also be found in RFC 1991.
PGP 5.x (formerly known as "PGP 3") uses Diffie-Hellman/DSS for key
management and digital signatures; IDEA, CAST, or 3DES for message
encryption; and MD5 or SHA for computing the message's hash value.
OpenPGP, described in RFC 2440, is an open definition of security software based on PGP 5.x.
(See more detail about PGP below in Section 5.5.)
|
| Privacy Enhanced Mail (PEM)
| Provides secure electronic mail over
the Internet and includes provisions for encryption (DES),
authentication, and key management (DES, RSA). May be superseded by
S/MIME and PEM-MIME. Developed by IETF PEM Working Group and defined in
four RFCs:
- RFC 1421: Part I, Message Encryption and Authentication Procedures
- RFC 1422: Part II, Certificate-Based Key Management
- RFC 1423: Part III, Algorithms, Modes, and Identifiers
- RFC 1424: Part IV, Key Certification and Related Services
|
| Private Communication Technology (PCT)
| Developed by Microsoft and Visa for
secure communication on the Internet. Similar to SSL, PCT supports
Diffie-Hellman, Fortezza, and RSA for key establishment; DES, RC2, RC4,
and triple-DES for encryption; and DSA and RSA message signatures. A
companion to SET.
|
| Secure Electronic Transactions (SET)
| A merging of two other protocols: SEPP
(Secure Electronic Payment Protocol), an open specification for secure
bank card transactions over the Internet, developed by CyberCash, GTE,
IBM, MasterCard, and Netscape; and STT (Secure Transaction Technology), a
secure payment protocol developed by Microsoft and Visa International.
Supports DES and RC4 for encryption, and RSA for signatures, key
exchange, and public-key encryption of bank card numbers. SET is a
companion to the PCT protocol.
|
| Secure Hypertext Transfer Protocol (S-HTTP)
| An extension to HTTP to provide secure
exchange of documents over the World Wide Web. Supported algorithms
include RSA and Kerberos for key exchange, DES, IDEA, RC2, and
Triple-DES for encryption.
|
| Secure Multipurpose Internet Mail Extensions (S/MIME)
| An IETF secure e-mail scheme intended to supercede PEM. S/MIME, described in RFCs 2311 and 2312, adds digital signature and encryption capability to Internet MIME messages.
|
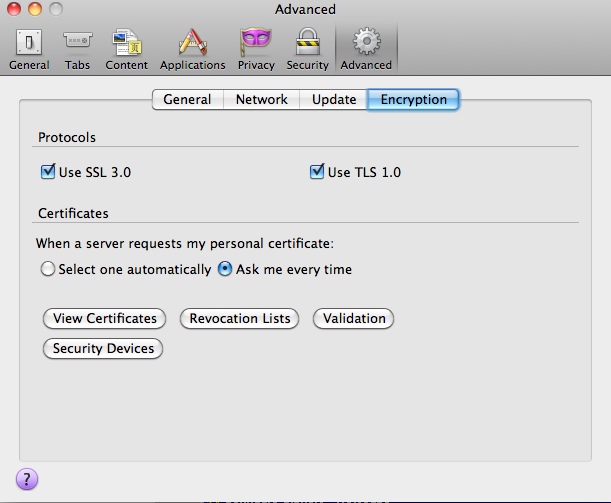
| Secure Sockets Layer (SSL) |
Developed by Netscape Communications to
provide application-independent security and privacy over the Internet.
SSL is designed so that protocols such as HTTP, FTP (File Transfer
Protocol), and Telnet can operate over it transparently. SSL allows both
server authentication (mandatory) and client authentication (optional).
RSA is used during negotiation to exchange keys and identify the actual
cryptographic algorithm (DES, IDEA, RC2, RC4, or 3DES) to use for the
session. SSL also uses MD5 for message digests and X.509 public-key
certificates. (Found to be breakable soon after the IETF announced
formation of group to work on TLS.) SSL version 3.0 is described in RFC 6101.
(See more detail about SSL below in Section 5.7.) |
| Server Gated Cryptography (SGC)
| Microsoft extension to SSL that
provides strong encryption for online banking and other financial
applications using RC2 (128-bit key), RC4 (128-bit key), DES (56-bit
key), or 3DES (equivalent of 168-bit key). Use of SGC requires a Windows
NT Server running Internet Information Server (IIS) 4.0 with a valid
SGC certificate. SGC is available in 32-bit Windows versions of Internet
Explorer (IE) 4.0, and support for Mac, Unix, and 16-bit Windows
versions of IE is expected in the future.
|
| Simple Authentication and Security Layer (SASL)
| (SASL) is a framework for providing
authentication and data security services in connection-oriented
protocols (a la TCP). It provides a structured interface and allows new
protocols to reuse existing authentication mechanisms and allows old
protocols to make use of new mechanisms.
It has been common practice on the Internet to permit anonymous access
to various services, employing a plain-text password using a user name
of "anonymous" and a password of an email address or some other
identifying information. New IETF protocols disallow plain-text logins.
The Anonymous SASL Mechanism (RFC 4505) provides a method for anonymous logins within the SASL framework.
|
| Simple Key-Management for Internet Protocol (SKIP) |
Key management scheme for secure IP
communication, specifically for IPsec, and designed by Aziz and Diffie.
SKIP essentially defines a public key infrastructure for the Internet
and even uses X.509 certificates. Most public key cryptosystems assign
keys on a per-session basis, which is inconvenient for the Internet
since IP is connectionless. Instead, SKIP provides a basis for secure
communication between any pair of Internet hosts. SKIP can employ DES,
3DES, IDEA, RC2, RC5, MD5, and SHA-1. |
| Transport Layer Security (TLS) |
TLS v1.0 is an IETF specification (RFC 2246)
intended to replace SSL. TLS v1.0 employs Triple-DES (secret key
cryptography), SHA (hash), Diffie-Hellman (key exchange), and DSS
(digital signatures). TLS v1.0 has been shown to be vulnerable to attack
and has been updated by v1.1 (RFC 4346) and v1.2 (RFC 5246.
TLS is designed to operate over TCP. The IETF developed the Datagram
Transport Layer Security (DTLS) protocol to operate over UDP. DTLS v1.2
is described in RFC 6347.
(See more detail about TLS below in Section 5.7.) |
| TrueCrypt |
Open source, multi-platform cryptography
software that can be used to encrypt a file, partition, or entire disk.
One of TrueCrypt's more interesting features is that of plausible deniability with hidden volumes or hidden operating systems.
(See more detail about TrueCrypt below in Section 5.11.) |
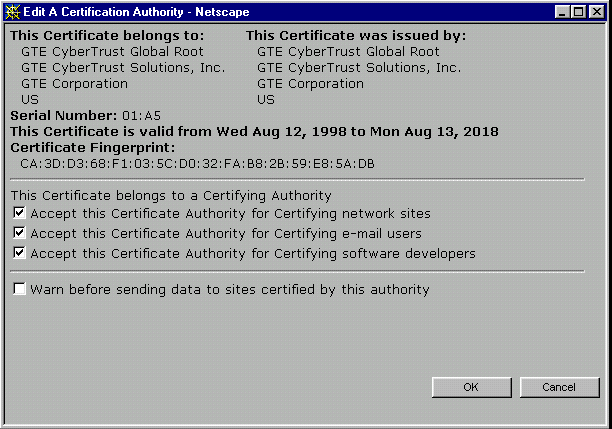
| X.509
| ITU-T recommendation for the format of
certificates for the public key infrastructure. Certificates map (bind)
a user identity to a public key. The IETF application of X.509
certificates is documented in RFC 2459. An Internet X.509 Public Key Infrastructure is further defined in RFC 2510 (Certificate Management Protocols) and RFC 2527 (Certificate Policy and Certification Practices Framework).
|